Since we spend almost a third of our lives online, many of our habits and behaviors take place on the internet. Like regular habits, they can be both good and bad. Unlike regular habits, quitting lousy internet habits rarely ends up on our New Year’s resolutions list. It’s time we changed that.
Checking your bank balance while using free public Wi-Fi, downloading files from sketchy websites, and, of course, creating easy-to-guess passwords because “no one cares about hacking my accounts” are some bad habits you may practice. It’s time you stopped justifying these risky behaviors. Here’s a helpful list of the top 10 bad online habits you should work on this year.
Account security mistakes
Do lousy passwords used all over the internet and written down on a sticky note ring a bell? You may need better account security habits.
1. Using the same password for everything
Reusing the same password on multiple accounts is one of the worst things you can do to your online security. It’s like using the same key to lock your home, car, and deposit box – even after someone stole the key and could have made a copy.
With millions of records exposed in data breaches every quarter, it’s easier than ever for hackers to get passwords. If you use a single password for every login, cybercriminals can use the password leaked in one data breach to access all your other online accounts.
So if you quit one bad internet habit this year, make it this one.
What to do instead:
Create a unique password for every account, and use a password manager to store (and remember) these passwords for you.
2. Setting “123456” as your password
If you use “123456” as your password, you’re one of the 1.5M people who used and lost this password in 2022. The only password worse than “123456” is the password “password.” And hackers can crack both in under a second.
Obvious number or character combinations and dictionary words are not good password material. Secure passwords should be impossible to guess for humans and take ages to brute force for computers.
What to do instead:
Never use “123456,” “password,” or “qwerty” as your password. Create a unique password that’s 12 or more characters in length, containing uppercase and lowercase letters as well as special symbols. You can use a password generator to make such passwords instantly.
3. Keeping passwords on sticky notes
Having a unique and robust password but keeping it on a sticky note or in another easily accessible plain-text form is not much better than using simple passwords like “123456” or reusing the same password for everything.
You may trust your family with your passwords, but other people visit your home too. Friends, their significant others and their kids, or home maintenance workers – you can’t always predict who will be at your home and take a look at your openly shared password.
If you take the same practice to your workplace, it’s even worse – a bigger stream of people pass by your desk and computer. Sticky notes are no good for remembering private information.
What to do instead:
Invest in a password manager. You won’t need sticky notes or other forms of insecure password-keeping. The password manager will secure your passwords with next-generation encryption and even
4. Not using two-factor authentication
If passwords are the first line of defense for your online accounts, then two-factor authentication (2FA) is the second.
How does it work? After you enter your password, your account requires a one-time passcode or other confirmation (e.g., clicking on a notification) that you, not someone else, are accessing the account.
What’s the point? If your password is exposed in a data breach, 2FA prevents hackers from accessing your accounts using the leaked password.
Two-factor authentication is available on most online services, including Google, Apple’s iCloud, Facebook, Instagram, Twitter, and NordVPN. But too many people don’t take advantage of this excellent security feature. Don’t be one of them.
What to do instead:
Enable 2FA on your accounts whenever it’s available. Usually, you can do so by visiting security settings on any particular website or using a third-party app, such as Google Authenticator. You can also autofill them, so you don’t need to type them each time.
Accidental exposure of sensitive data
Some bad internet habits are conscious choices. You know “password” is a terrible password, but you keep using it because it’s easy. Some behaviors, however, may not be that obvious and lead to accidental exposure of your most private information.
5. Clicking on links in strange emails
Many cyberattacks are successful because people open ransom emails they receive from strangers. And most strangers that send such emails are scammers and hackers.
Scammers use phishing and social engineering techniques to urge you to click on their links. These links take you to fake websites created to steal your passwords, credit card details, and other sensitive information.
What to do instead:
Don’t know or trust the source? Don’t click the link. When you do know the sender, double-check whether the link looks natural and whether receiving it makes sense because email addresses often get spoofed.
6. Visiting HTTP sites
The “HTTP” prefix you see on the website address usually indicates that your connection is not secure. What does it mean? Snoopers could see the data you share with that website.
HTTP websites are dangerous for online payments and cases when you need to provide personal information. That’s why most browsers warn you when you visit such websites.
What to do instead:
To stay on the safe side, only browse sites that use an SSL – an encrypted connection, indicated by HTTPS. If you have no choice but to visit unprotected websites, enable a VPN extension first to secure your traffic.
7. Checking your bank account on public Wi-Fi
Like HTTP sites, public wireless networks usually lack proper protection. They leave you open to man-in-the-middle attacks and other nefarious ways for hackers and snoopers to get your information. Anyone could intercept your banking credentials or other sensitive data if you visit insecure sites on such a network.
What to do instead:
When on public Wi-Fi, don’t check sensitive information, especially if it’s work or money related. Or better still — get a virtual private network (VPN) and keep your communications safe even on public Wi-Fi.
8. Not making backups
No one thinks about backups much until the device gets stolen, infected by malware, or malfunctions. It’s easy to replace the old machine with a new one, but what about all the important files and photos you kept on it?
Unless you have them safely backed up, they are gone or extremely difficult (and costly) to retrieve. The damage is much less detrimental if you have copies of that data safely residing on another device, hard drive, or cloud.
What to do instead:
Make regular backups. When possible, have at least two copies and keep them in different storage (e.g., one on the hard drive and another in the cloud). You can keep them encrypted for extra protection.
9. Uploading files to the cloud as they are
The cloud saves precious storage, and most devices automatically sync your files to the cloud. But is your data safe while sitting comfy in the cloud? Often, it’s not.
Remember Britney Spears’ iCloud incident? If someone steals your cloud credentials, they can access everything you keep in the cloud.
Moreover, most cloud companies can access your files if they want. A nosy employee with enough access privileges may snoop around in your private files. Or they may have questionable privacy practices enabling third parties to access your data.
Finally, cloud companies are vulnerable to cyberattacks and data breaches which may put your sensitive data in the wrong hands.
What to do instead:
Encrypt your files before uploading them to the cloud or use services that guarantee end-to-end encryption, such as NordLocker. NordLocker allows you to access encrypted data via cloud, or sync files across all devices.
10. Agreeing to all terms and conditions on software install
Reading the terms and conditions every time you want to install a new app is a real pain. No one’s surprised you hit “agree” without looking at what’s written there. However, reading at least a part of those terms and conditions should be your new habit.
By agreeing to the terms without reading them, you may be allowing the software to:
- collect and sell information about you.
- listen to your conversations.
- install additional software you don’t need.
Agreeing to all terms impacts your privacy, security, and device performance in the long run.
What to do instead:
Read the terms and conditions before clicking “agree,” focusing on the parts related to data collection and privacy.


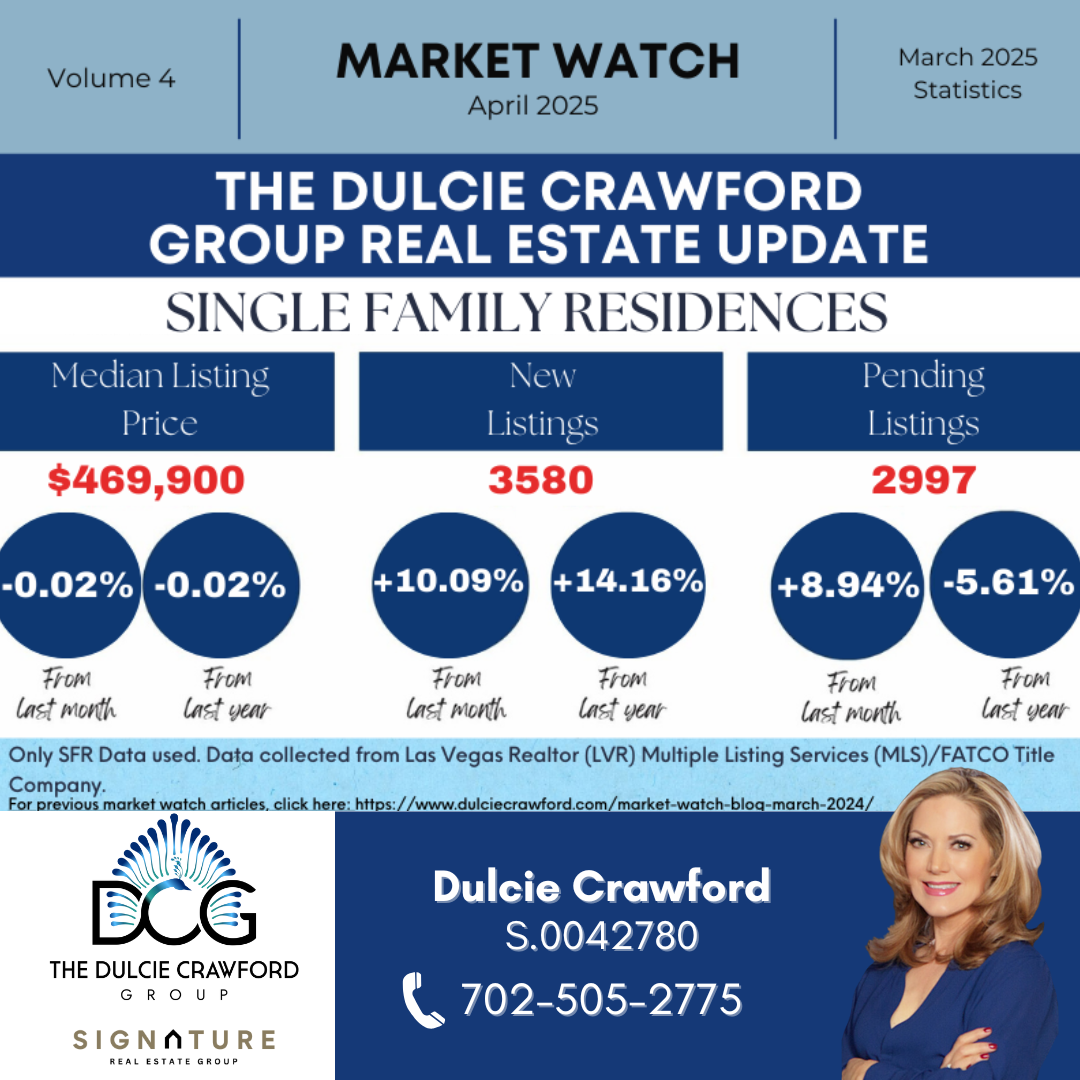
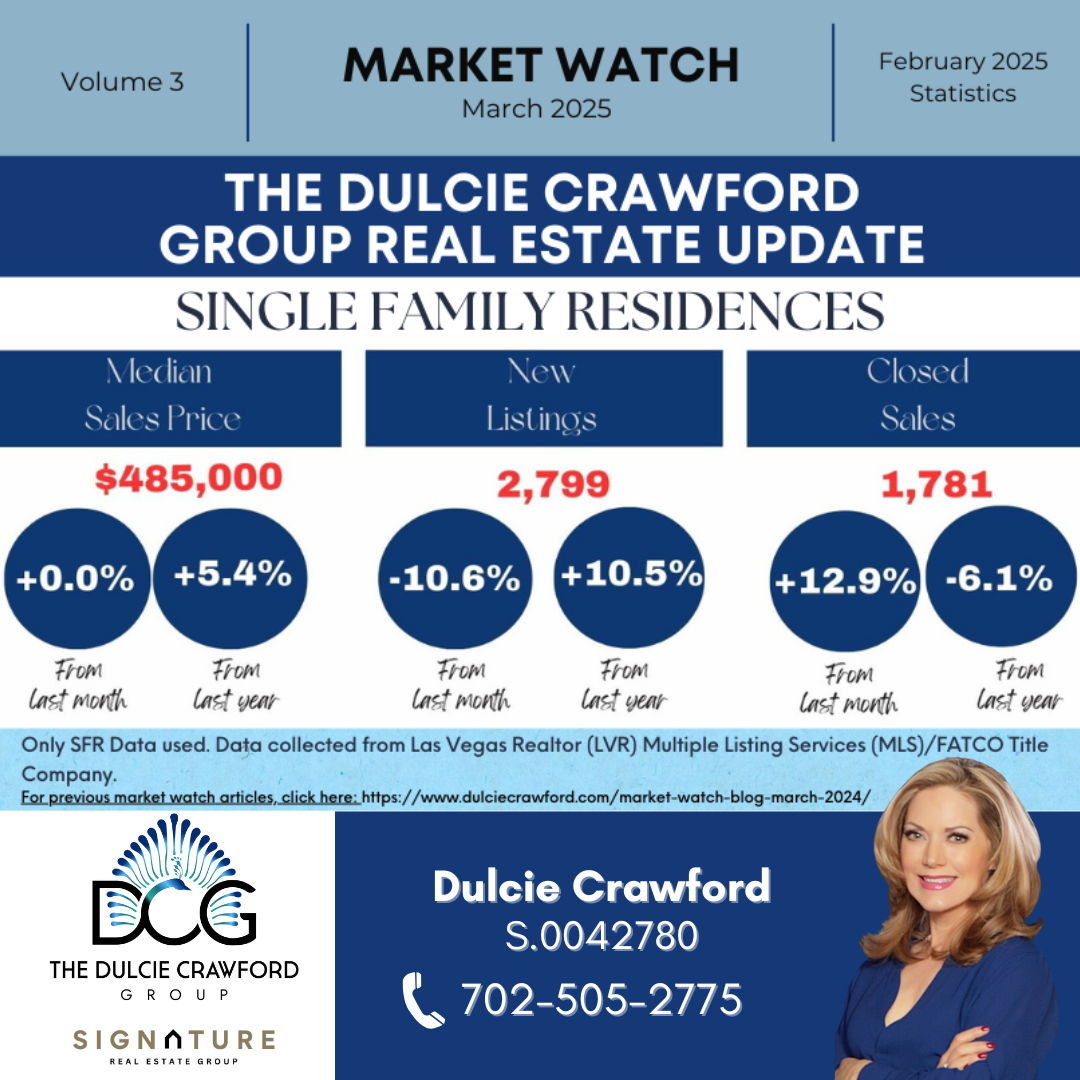
Experience Excellence!
The Dulcie Crawford Group.
If you are interested in buying real estate in the Las Vegas and Henderson area, please contact Dulcie! Dulcie’s dedication to her clients and ethical standards has earned her 5 star ratings and Premier Agent Status with Zillow.com real estate portal. You will be assured a professional experience when buying or selling Real Estate with Real Estate with The Dulcie Crawford Group.